Publication Title #1
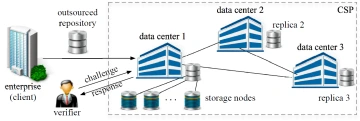
Cloud computing promises ubiquitous, on-demand access to an expandable pool of computing resources, including storage, computation, and software services. However, the risk of losing outsourced data due to failures or security breaches exposes cloud users to grave legal, financial, and business liabilities. In this project, we aim at developing provably secure, privacy-preserving methods for verifying the fault-tolerant storage of voluminous data at remote repositories. We focus on the Infrastructure-as-a-Service (IaaS) model, and in particular, a typical remote storage scenario in which the cloud storage provider (CSP) contractually agrees to maintain a large repository with a certain degree of reliability, outlined in a Service Level Agreement (SLA). This project focuses on a comprehensive research agenda at the cross-paths of security, error-correction coding, and networking that aims at achieving verifiability, privacy, and resource efficiency of remote reliable storage at both the logical level (storage of data and redundancy) and physical level (distribution across physical devices and locations).
Publication Title #2
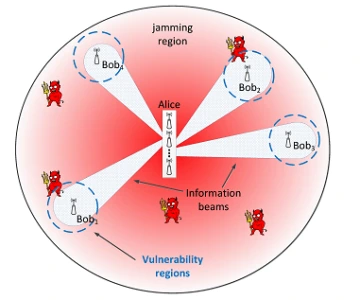
Cloud computing promises ubiquitous, on-demand access to an expandable pool of computing resources, including storage, computation, and software services. However, the risk of losing outsourced data due to failures or security breaches exposes cloud users to grave legal, financial, and business liabilities. In this project, we aim at developing provably secure, privacy-preserving methods for verifying the fault-tolerant storage of voluminous data at remote repositories. We focus on the Infrastructure-as-a-Service (IaaS) model, and in particular, a typical remote storage scenario in which the cloud storage provider (CSP) contractually agrees to maintain a large repository with a certain degree of reliability, outlined in a Service Level Agreement (SLA). This project focuses on a comprehensive research agenda at the cross-paths of security, error-correction coding, and networking that aims at achieving verifiability, privacy, and resource efficiency of remote reliable storage at both the logical level (storage of data and redundancy) and physical level (distribution across physical devices and locations).
Publication Title #3
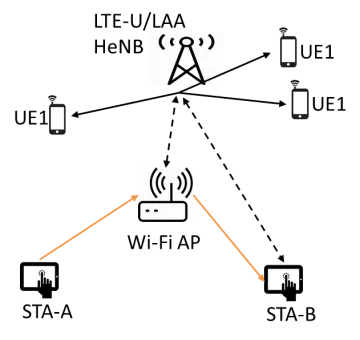
Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text
Publication Title #4
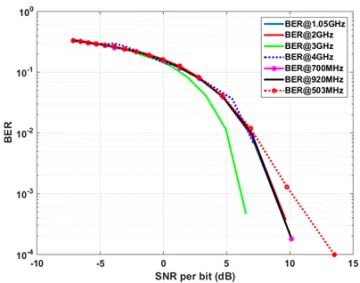
Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text Sample text
